Digital Transformation
We help your organization address its digital transformation most pressing challenges across people, process, technology, and policies by taking a top-down functional approach and translating cyber risks into business risks.

By incentivizing a community of practitioners to make iterative improvements on Security and Digital Transformation through the sharing of ideas and collective action, we hold people accountable at the core. This mindset contributes to diffuse a pervasive security and compliance culture across every level of the organization. We will help you to identify your organization’s positions on the Digital Transformation, Identity and Access Management, and Cybersecurity maturity curves. Through iterative processes, we will recommend the best course of action, help you prioritize and make the right technological choices adapted to your business and technology requirements and needs. We will create a virtuous feedback loop of continuous diagnostics, mitigation, and remediation, which we would progressively automate in a self-reinforcing mechanism.
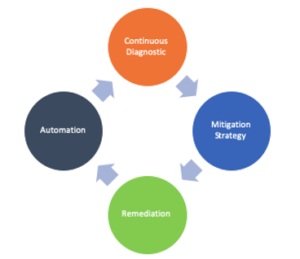

Creating a virtuous feedback loop of continuous diagnostics, mitigation, and remediation

Developing automation and self-reinforcing mechanisms for economies of scale and scope

Disseminating a Security and Compliance culture across every level of the organization

Moving up the Digital Transformation, Cybersecurity, and Identity and Access Management maturity curves
What Questions Can We Help You Answer?

Digital Transformation programs may relate to migration to the cloud, implementing a company-wide remote working practice, developing an End-to-End Identity platform, launching an application or software development project. During those transition phases, companies are the most vulnerable. By approaching Cybersecurity from the perspective of Digital Transformation, we understand that systems should be secure by design and that security should be built into systems and applications from the ground-up rather than reactively after security flaws have accumulated and serious breaches occurred.
The Cybersecurity paradigm is now a matter of when-not-if a breach will occur. It is thus essential that organizations be aware of the cyber threats they face. Who are the threat agents, their motivations, and their levels of sophistication, and which attack vectors do they use? Which attack surfaces do they target, and what could be the impact? Companies should be able to map threats to assets to vulnerabilities to controls and prioritize in the right direction across the people, process, and technology framework while designing the right policies.
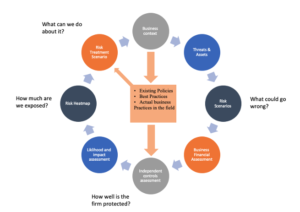
How can my organization move up the security maturity curve, from reactive security to proactive and adaptive security while addressing its digital transformation challenges?
How can we create a virtuous feedback loop of continuous diagnostics, mitigation, and remediation which we could progressively automate in self-reinforcing mechanisms?
What are my organization's most pressing digital transformation challenges and how can I address them in the light of better security, resiliency, adaptability, user-friendliness, and productivity?
How can I integrate the best processes and technology such as identity and access management in a way that is coherent with my information security policy?
How can I define long-lasting security roadmaps to sustainable cybersecurity?
How can we deploy real-time monitoring capabilities on our systems and which predictive analytics can we leverage to anticipate threats?
Which policies are supporting my people, process, and technology framework and how can we address this framework from the perspective of each of its components?
How can I implement a sustainable and optimal identity, governance and access management program in the context of my enterprise digital transformation?
How can I implement a secure remote working program while addressing my company's digital transformation most pressing challenges?
Key Elements

Technology should support sound security processes through threat modeling and the Risk Management Lifecycle. By embedding Cybersecurity into your Digital Transformation program, you will develop systems and applications that are secure-by-design while reconciling security, privacy, and usability, creating change dynamics, and driving real action.

Translating Cyber Risks into Business Risks and providing and End-to-End platform in Cybersecurity and Digital Transformation

Long-term security roadmap related to upstream and downstream metrics to measure the success of the implementation

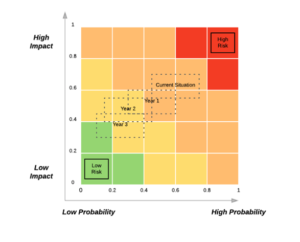
Reducing the Cyber-Value-at-Risk and Increasing Cyber resiliency over time by reducing the likelihood and impact of risk factors at the local and aggregate levels

Finding a commonality of views, full trust and stakeholder alignment around the execution of a common security roadmap while creating bridges between IT and business functions
What results can you expect?
Through a comprehensive Risk Treatment Roadmap and Framework aligned with Risk Management and Security Controls, your organization will move up the Digital Transformation Maturity curve while lowering overall risk levels and the associated Cyber-Value-at-Risk.
B to A
Increase in security score and decrease in the likelihood of being breached
+20%
Increase in productivity
